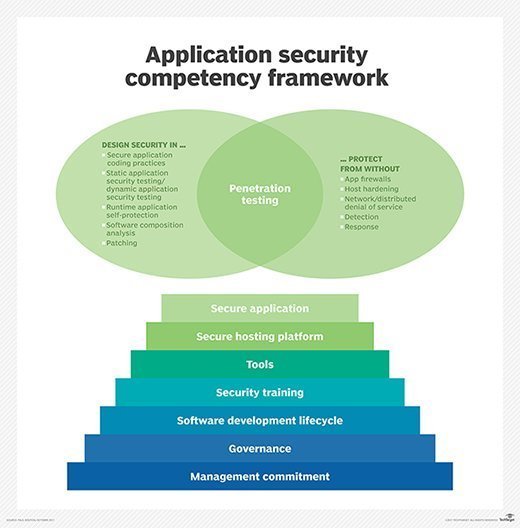
In addition to the basic auditing framework laid out in this article it is recommended to use a penetration testing framework that applies to all mobile apps prior to their release.
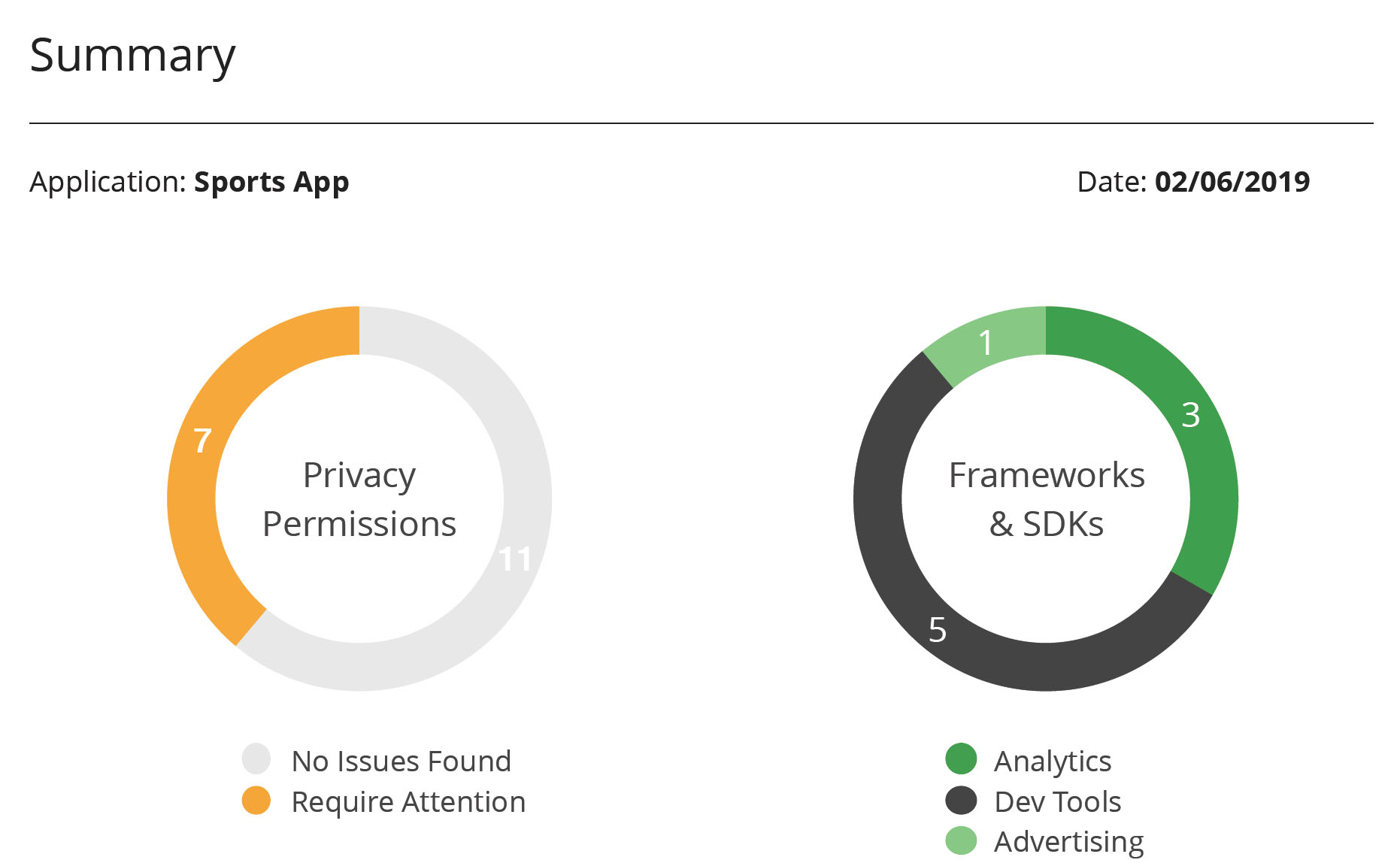
Mobile app security audit framework.
Start managing them to ensure security and compliance.
Cyber security framework for urban cooperative banks.
Sebi cyber security and cyber resilience framework uidai aua kua.
Deep analysis of mobile apps at scale.
Mobile app security audit framework mohammed j.
More and more users and businesses use smartphones to communicate but also to plan and organize their users work and also private life.
Our mobile application security testing service leverages application mapping reverse engineering and proprietary tools to identify business logic and technical vulnerabilities in your mobile applications.
Drozer is a comprehensive security audit and attack framework for android.
In addition penetration testing must be performed as the mobile app is updated and newer technology is put in place to support the app.
As a result of companies digitalizing their frameworks and services corporate and personal data are now extensively accessed by mobile devices exposing them to a whole new range of mobile.
The mobile security testing guide mstg provides verification instructions for each requirement in the masvs as well as security best practices for apps on each supported mobile operating system currently android and ios.
He has spearheaded multinational global audits in several areas including enterprise resource.
Audit mobile apps security level.
Identify the cloud apps iaas and paas services used by your organization.
Investigate usage patterns assess the risk levels and business readiness of more than 16 000 saas apps against more than 80 risks.
Sven schleier jeroen willemsen carlos holguera.
Mobile security or more specifically mobile device security has become increasingly important in mobile computing of particular concern is the security of personal and business information now stored on smartphones.
Mobile data transiting between mobile devices applications servers etc.
The cloud app security framework.
Have you considered the threat posed by the android app that supports your business function or android devices being used as part of your byod strategy.
Hook any function spy on crypto apis or trace private application code no source code needed.
A standard for mobile app security which outlines the security requirements of a mobile application.
Khan cisa crisc cipm is a global audit manager at baxter a global medical device company.
A checklist which allows easy mapping and scoring of the requirements from the mobile application security verification standard based on the mobile security testing guide.
Discover and control the use of shadow it.
Edit hit save and instantly see the results.
It is also useful as a standalone learning resource and reference guide for mobile application security testers.
Inject your own scripts into black box processes.
He works with the chief audit executive chief information security officer and chief privacy officers.